Security
Manage operating system firewall, SSH service, operating system root user, Brute force protection, Compiler Access, Anti Intrusion, System Hardening, view SSH login logs
Firewall
Manage network access to this server. The
defaultfirewall rule is todeny access.
External access is required and the corresponding port or IP rules need to be allowed.

Turn on to Firewall :
Turn offthe system firewall. It is not recommended to turn it off unless necessary.Turn on to Block ICMP :
Disable ping. After it is turned on, other devices cannot ping this machine.Site Logs : Display the log path and size of the website. Click
Clearto clear.
Port rule
Deny or allow IP access to the port.
| Function | Describe |
|---|---|
Add Port Rule | Add a port rule |
| Import rules | Upload files and import port rules |
| Export rules | Export port rules and download the file |
| All directions | View rules for all directions |
| Inbound | Click to view inbound directions |
| Outbound | Click to view outbound directions |
| Protocol | Port protocol type:TCP/UDP,TCP,UDP |
| Port | port range is1-65535 |
| Status | Port status:ListeningorNot Listening, some ports can be viewed using Details |
| Strategy | portAlloworDeny Strategy. |
| Direction | port InboundorOutbound Directions |
| Source IP | Deny or allow sourcesAllorSpecify IPVisits |
| Remarks | Remarks on port rules |
| Add Time | Time to add rules |
| Edit | Edit port rules |
| Delete | Delete port rule |
Add Port Rule or Edit
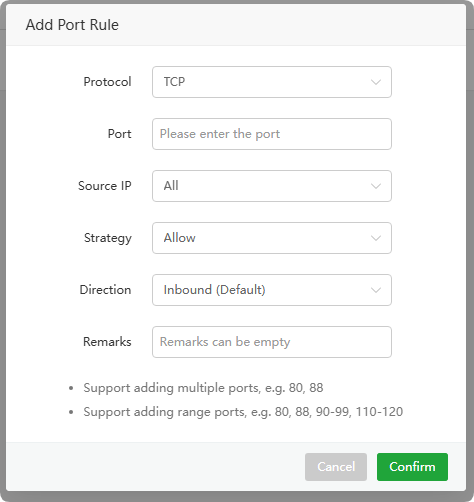
Protocol : Select protocol type optional
TCP,TCP/UDP,UDPPort : Input port, the port range is
1-65535Source IP : Source IP is selectable
AllorSpecify IPStrategy : Port policy is selectable
AlloworDenyDirection : Direction optional
InboundorOutboundRemarks : Comments on this rule
IP rules
Deny or allow IP access.

| Function | Describe |
|---|---|
| Add ip Rule | Add an IP rule |
| Import rules | Upload files and import IP rules |
| Export rules | Export IP rules and download the file |
| Inbound | Click to view inbound directions |
| Outbound | Click to view outbound directions |
| Source IP | BlockorReleaseSource IP |
| Strategy | IP policyBlockorRelease |
| Direction | IP policyInboundorOutboundDirections |
| Remarks | Notes on IP rules |
| Add Time | Time to add IP rules |
| Edit | Edit IP Rules |
| Delete | Delete IP rules |
Block: access
DenyRelease:
Allowaccess
Add ip Rule or Edit
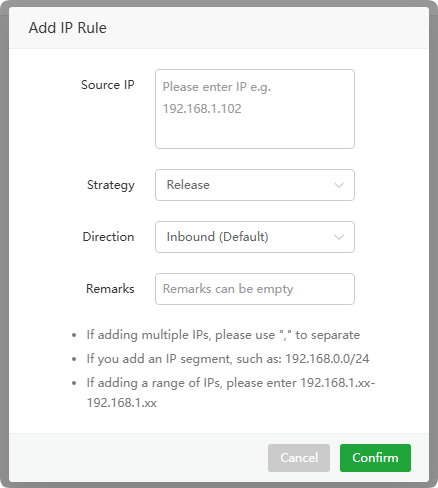
Source IP : Enter the source IP
Strategy : For the source IP
BlockorReleaseReleaseDirection : Direction optional
InboundorOutboundRemarks : Comments on this rule
Port forward
Forward access traffic from one port to another port on the local machine or the port of the target server.
Typically used to implement Network Address Translation (NAT), which forwards external requests to a specific device or service on the internal network.
| Function | Describe |
|---|---|
| Add port forward | Add a port forward rule |
| lmport rules | Upload files and import port forward rules |
| Export rules | Export port forward rules and download the file |
| Protocol | Port protocol type:TCP,UDP |
| Source port | source port1-65535 |
| Target IP | Forward to target IP |
| Target port | Port forwarded to target |
| Remarks | Comments on this rule |
| Add Time | Time to add rules |
| Edit | Edit port forward rules |
| Delete | Delete port forward rules |
Add port forward or Edit
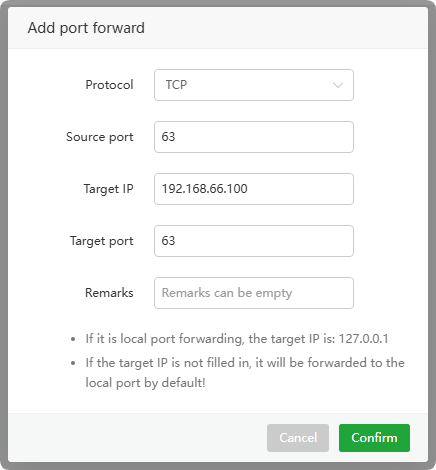
Protocol : Select the protocol of the port source:
TCPorUDPSource port : The source port of the traffic
Target IP : The
target IPto forward to or127.0.0.1(localhost)Target port : the port to forward to
Remarks : Comments on this rule
Area rules
Deny or allow IP segments in the region to access the server.
Area rules default to
Allow
Since IP addresses are not 100% accurate, please use them with caution. It is recommended to release your IP segment first and then ban it.

| Function | Describe |
|---|---|
| Add area rule | Add an Area rule |
| Import rules | Upload files and import Area rules |
| Export rules | Export Area rules and download the file |
| Area | BlockArea |
| Strategy | Area strategyBlock |
| Port | to AreaAll portsorSpecified portBlock Visit |
| Add Time | Time to add rules |
| Edit | Edit Area Rules |
| Delete | Delete Area Rules |
Add area rule or Edit
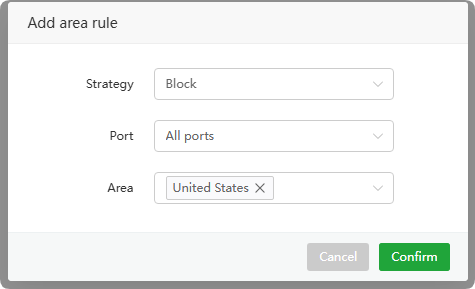
Strategy :Block rules
Port : Select the area
All portsorSpecified portForbidden accessArea : Select one or more Areas to deny access
SSH
SSH login settings, SSH login log.
SSH allows remote users to log into the server over the network and execute commands.

Turn on SSH :
Enableorstopthe SSH service. It will be enabled automatically afterrestartingthe server.SSH Login Details : SSH login log, showing the
totalortoday'snumber of successful and failed logins.
Basic setup (SSH)
SSH Password login : Allow or prohibit
root userpassword loginSSH key login :
EnableordisableSSH key loginSSH port : The default port is
22. It is recommended to change it to other ports to avoid being scanned.Root login Settings
- yes -
keys and passwords - no -
no login - without-password -
only key login - forced-commands-
only-can onlyexecute commands
- yes -
Root password :
resetroot passwordRoot key :
Viewanddownloadthe public key of the root keySSH login alarm : After the
root userlogs in, an alarm message is sent.
SSH login logs
If malicious access is found (a lot of
failedlogins):
- It is recommended to
modify the SSH portto avoid being attacked. Please release the port in the server provider's security group before modification.- In the Security menu, turn on IP Address-based Protection (Based on ssh) under Brute force protection.

Refresh : Retrieve the latest data
ALL : View all login logs
Success : View successful login log
Failure : View failed login logs
IP:Port: Login IP and port
Place of attribution : Login area
User : Login user
Status : Login status
Operation time : Login time
Brute force protection

aaPanel Brute Force Protection :
EnableordisableaaPanel brute force protectionConfiguration
Username-based Protection (Based on aapanel)
For aaPanel users
- AAPanel brute-force cracking protection. When enabled, the user will be locked out when the
username or password is incorrectfor more than a certain number of times. - After locking a user, the user cannot log in and needs to wait for a certain period of time before unblocking, or use the command
bt 33to unblock.
- AAPanel brute-force cracking protection. When enabled, the user will be locked out when the
IP Address-based Protection (Based on ssh) {#IPAddress-basedProtection}
For operating system SSH users
- SSH brute-force cracking protection. When enabled, when the
IP addresserror exceeds a certain number of times, the IP address will be locked. - After locking the IP address, the
IP address cannot access server. Need to wait for a certain period of time before unblocking it, or use the commandipset del aapanel.ipv4.blacklist to replace it with an IP addressto unblock it.
- SSH brute-force cracking protection. When enabled, when the
Login History
- History Reports Display logs of failed SSH logins at the specified time
WhiteList : IP address whitelist, not affected by configuration, multiple IP addresses can be added.
- BlackList : IP address blacklist, prohibiting access to all ports of the server.
History Reports
Refresh : Get the latest data on SSH login failures
Remove Blocks and Clear Reports : Remove all bans and IP addresses and clear reports
Select a Report
Failed Logins : Display logs of failed SSH logins at the specified time

Blocked IP Addresses : Displays the blocked IP address and blocking time. Click
Unblockto unblock it.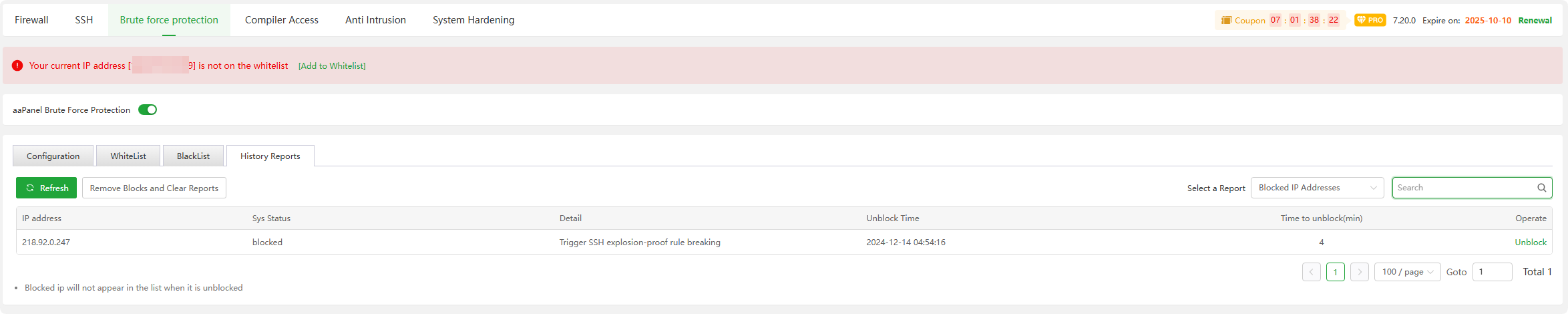
Compiler Access
Disable specified users from using the Gcc compiler.

Anti Intrusion
Disable user operation commands for specified users and record traces

Intrusion Prevention Switch : Turn Anti Intrusion on or off
Intrusion interception times : Display the number of times this plug-in intercepts intrusion
Protection days : Displays the number of days this plug-in protects the operating system
Overview
User: Display
all usersexisting in the operating systemTotal: Displays the
totalnumber of commands executed by this userToday: Displays the total number of commands executed by users
todayProtection:
Turn on or off protectionfor this user. Please do not turn it on for ordinary users, as it will result in the inability to log in or execute commands.Log:
Turn on or off loggingfor this userRemark; displays user notes and whether they can log in
- Logs : View user protection log records
Process whitelist
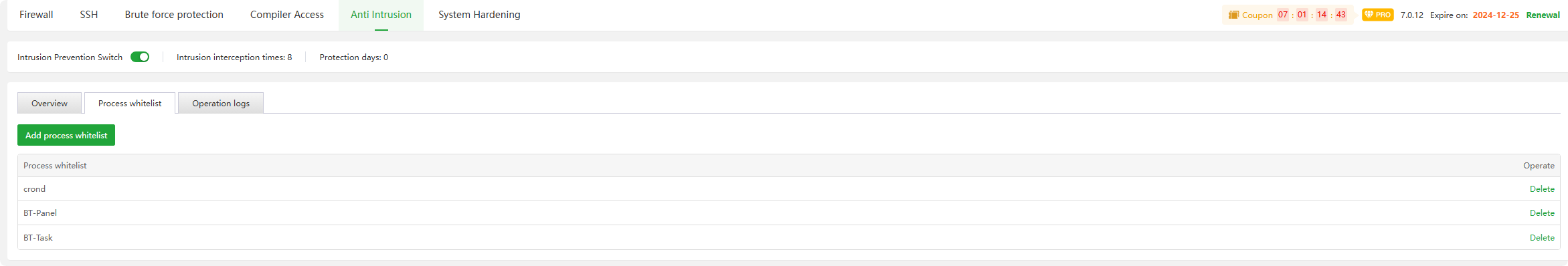
- Add process whitelist : Add process whitelist,
protection is invalid for this process.
- Delete : Delete process whitelist
- Add process whitelist : Add process whitelist,
Operation logs : View Anti Intrusion operation log

System Hardening

System hardening :
Turn onoroffSystem HardeningProtection :
Name: Protection project name
Service:
Protect system services. Once enabled, services cannot beaddedordeleted, and some software cannot beinstalled!ENV:
Protects user environment variablesfrom being modified. User environment variables cannot be customized after being enabled!User:
Protect users. After turning it on, you will not be able toadded,deletedusers andmodified user passwords!Directory:
Protect key system filesfrom modification and replacement!Crontab:
Protect Cron tasksfrom being tampered with. Once enabled, Cron tasks cannot beadded,modified, ordeleted!SSH:
Protect SSHfrom brute force cracking and record user login logsAbnormal process:
Abnormal processis detected and the process isautomatically terminated
Desc : Protect the
descriptionof this projectStatus: This project is
onoroff
- Modify :
Addordeletethe protection specified path of this project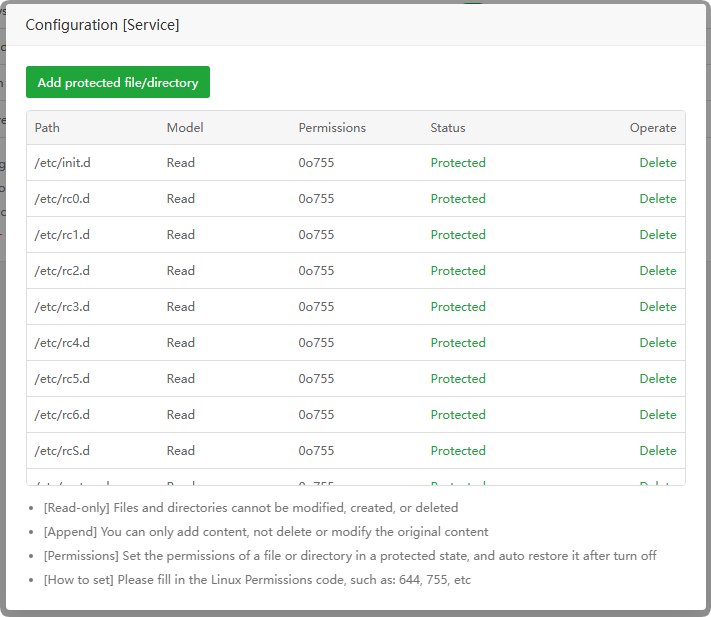
Block IP :
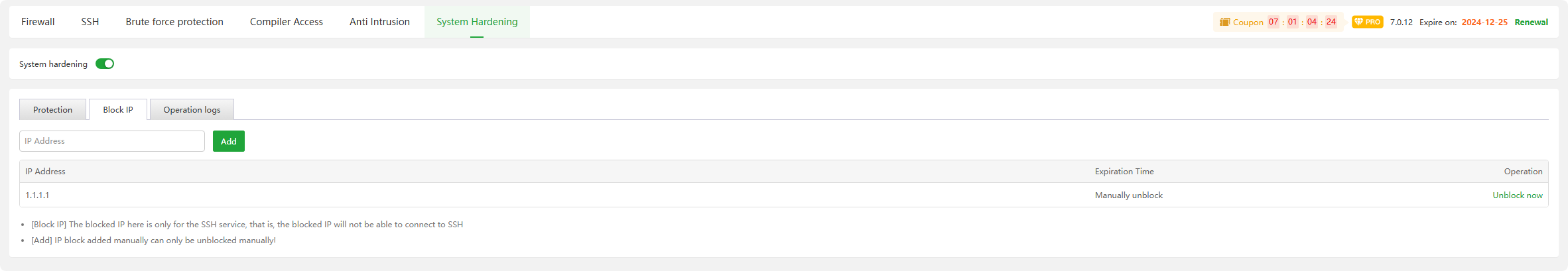
Add : IP addresses that are
prohibitedfrom beingused by SSHservicesUnblock now : Unblock the corresponding IP address
Operation logs : View System Hardening operation log
