Hello, no changes will be made by default. How did you test it?
The mail server TLS port and SSL port will change
aaPanel_Kern Every time I update the mail server certificate, my PHP site TLS 465 port cannot connect, but 587 can connect. Sometimes TLS 465 can connect, which is strange.
After updating the certificate, will trying to directly save the certificate once resolve the issue?
aaPanel_Kern Saving the certificate didn't solve the problem. I could only solve it by using a port. For example, the original TLS port was 465 and now I can connect using 587.
openssl s_client -connect mail.site.net:587 -starttls smtp Show Verify return code: 0 (ok)
openssl s_client -connect mail.site.net:465 -starttls smtp Always Show CONNECTED(00000003)
Hello, check if the port is in use? Are the corresponding ports open in the system firewall and server provider's security group?
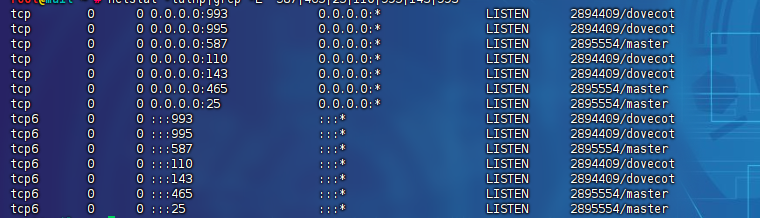
netstat -tulnp|grep -E "587|465|25|110|995|143|993"
This seems normal. Have you tried restarting postfix? Is there a server security group? Are the relevant ports allowed?
- Edited
Hi @aaP_greatvpn, hope I can help you on that. Can you share your /etc/postfix/master.cf please?
- Edited
#
# Postfix master process configuration file. For details on the format
# of the file, see the master(5) manual page (command: "man 5 master" or
# on-line: http://www.postfix.org/master.5.html).
#
# Do not forget to execute "postfix reload" after editing this file.
#
# ==========================================================================
# service type private unpriv chroot wakeup maxproc command + args
# (yes) (yes) (no) (never) (100)
# ==========================================================================
smtp inet n - n - - smtpd
#smtp inet n - n - 1 postscreen
#smtpd pass - - n - - smtpd
#dnsblog unix - - n - 0 dnsblog
#tlsproxy unix - - n - 0 tlsproxy
submission inet n - n - - smtpd
-o syslog_name=postfix/submission
-o smtpd_tls_security_level=encrypt
-o smtpd_sasl_auth_enable=yes
-o smtpd_tls_auth_only=yes
# -o smtpd_reject_unlisted_recipient=no
# -o smtpd_client_restrictions=$mua_client_restrictions
# -o smtpd_helo_restrictions=$mua_helo_restrictions
# -o smtpd_sender_restrictions=$mua_sender_restrictions
# -o smtpd_recipient_restrictions=
-o smtpd_relay_restrictions=permit_sasl_authenticated,reject
-o milter_macro_daemon_name=ORIGINATING
smtps inet n - n - - smtpd
-o syslog_name=postfix/smtps
-o smtpd_tls_wrappermode=yes
-o smtpd_sasl_auth_enable=yes
# -o smtpd_reject_unlisted_recipient=no
# -o smtpd_client_restrictions=$mua_client_restrictions
# -o smtpd_helo_restrictions=$mua_helo_restrictions
# -o smtpd_sender_restrictions=$mua_sender_restrictions
# -o smtpd_recipient_restrictions=
-o smtpd_relay_restrictions=permit_sasl_authenticated,reject
-o milter_macro_daemon_name=ORIGINATING
#628 inet n - n - - qmqpd
pickup unix n - n 60 1 pickup
cleanup unix n - n - 0 cleanup
qmgr unix n - n 300 1 qmgr
#qmgr unix n - n 300 1 oqmgr
tlsmgr unix - - n 1000? 1 tlsmgr
rewrite unix - - n - - trivial-rewrite
bounce unix - - n - 0 bounce
defer unix - - n - 0 bounce
trace unix - - n - 0 bounce
verify unix - - n - 1 verify
flush unix n - n 1000? 0 flush
proxymap unix - - n - - proxymap
proxywrite unix - - n - 1 proxymap
smtp unix - - n - - smtp
relay unix - - n - - smtp
-o syslog_name=postfix/$service_name
# -o smtp_helo_timeout=5 -o smtp_connect_timeout=5
showq unix n - n - - showq
error unix - - n - - error
retry unix - - n - - error
discard unix - - n - - discard
local unix - n n - - local
virtual unix - n n - - virtual
lmtp unix - - n - - lmtp
anvil unix - - n - 1 anvil
scache unix - - n - 1 scache
#
# ====================================================================
# Interfaces to non-Postfix software. Be sure to examine the manual
# pages of the non-Postfix software to find out what options it wants.
#
# Many of the following services use the Postfix pipe(8) delivery
# agent. See the pipe(8) man page for information about ${recipient}
# and other message envelope options.
# ====================================================================
#
# maildrop. See the Postfix MAILDROP_README file for details.
# Also specify in main.cf: maildrop_destination_recipient_limit=1
#
#maildrop unix - n n - - pipe
# flags=DRhu user=vmail argv=/usr/local/bin/maildrop -d ${recipient}
#
# ====================================================================
#
# Recent Cyrus versions can use the existing "lmtp" master.cf entry.
#
# Specify in cyrus.conf:
# lmtp cmd="lmtpd -a" listen="localhost:lmtp" proto=tcp4
#
# Specify in main.cf one or more of the following:
# mailbox_transport = lmtp:inet:localhost
# virtual_transport = lmtp:inet:localhost
#
# ====================================================================
#
# Cyrus 2.1.5 (Amos Gouaux)
# Also specify in main.cf: cyrus_destination_recipient_limit=1
#
#cyrus unix - n n - - pipe
# user=cyrus argv=/usr/lib/cyrus-imapd/deliver -e -r ${sender} -m ${extension} ${user}
#
# ====================================================================
#
# Old example of delivery via Cyrus.
#
#old-cyrus unix - n n - - pipe
# flags=R user=cyrus argv=/usr/lib/cyrus-imapd/deliver -e -m ${extension} ${user}
#
# ====================================================================
#
# See the Postfix UUCP_README file for configuration details.
#
#uucp unix - n n - - pipe
# flags=Fqhu user=uucp argv=uux -r -n -z -a$sender - $nexthop!rmail ($recipient)
#
# ====================================================================
#
# Other external delivery methods.
#
#ifmail unix - n n - - pipe
# flags=F user=ftn argv=/usr/lib/ifmail/ifmail -r $nexthop ($recipient)
#
#bsmtp unix - n n - - pipe
# flags=Fq. user=bsmtp argv=/usr/local/sbin/bsmtp -f $sender $nexthop $recipient
#
#scalemail-backend unix - n n - 2 pipe
# flags=R user=scalemail argv=/usr/lib/scalemail/bin/scalemail-store
# ${nexthop} ${user} ${extension}
#
#mailman unix - n n - - pipe
# flags=FR user=list argv=/usr/lib/mailman/bin/postfix-to-mailman.py
# ${nexthop} ${user}- Edited
aaP_radipta289
The problem is actually very simple, sometimes the ports of TLS and SSL are reversed, and sometimes they are normal. and the use is normal.
- Edited
aaP_greatvpn
I see now, you're testing the port with
openssl s_client -connect mail.site.net:465 -starttls smtp
Port 465 expects a direct SSL/TLS connection without the STARTTLS command, so that's why the STARTTLS handshake did not proceed as expected.
Try testing port 465 with this instead (without the -starttls smtp)
openssl s_client -connect mail.site.net:465
It looks fine to me.
Note:
Port 587 is used for SMTP submission with STARTTLS
Port 465 is used for SMTPS (SSL/TLS wrapper mode)
- Edited
```openssl s_client -connect mail.picgo.net:465 -starttls smtp
CONNECTED(00000003)
Didn't find STARTTLS in server response, trying anyway...
write:errno=32
---
no peer certificate available
---
No client certificate CA names sent
---
SSL handshake has read 0 bytes and written 23 bytes
Verification: OK
---
New, (NONE), Cipher is (NONE)
Secure Renegotiation IS NOT supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
Early data was not sent
Verify return code: 0 (ok)`
``openssl s_client -connect mail.picgo.net:465
CONNECTED(00000003)
depth=2 C = US, O = Internet Security Research Group, CN = ISRG Root X1
verify return:1
depth=1 C = US, O = Let's Encrypt, CN = R10
verify return:1
depth=0 CN = picgo.net
verify return:1
---
Certificate chain
0 s:CN = picgo.net
i:C = US, O = Let's Encrypt, CN = R10
1 s:C = US, O = Let's Encrypt, CN = R10
i:C = US, O = Internet Security Research Group, CN = ISRG Root X1
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIFATCCA+mgAwIBAgISBGJaZANwlGieWetgG0sg6BJDMA0GCSqGSIb3DQEBCwUA
MDMxCzAJBgNVBAYTAlVTMRYwFAYDVQQKEw1MZXQncyBFbmNyeXB0MQwwCgYDVQQD
EwNSMTAwHhcNMjQxMTA3MTIwMjM2WhcNMjUwMjA1MTIwMjM1WjAUMRIwEAYDVQQD
EwlwaWNnby5uZXQwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDKlJZW
nxkH/uhYSldFbYziVrtluxFRNi+UpTFfgHQ1sTnMf+FNtklzxwZ4TeotikvsBeBP
6J+c9lhdKPGY+KXqwpMRVqo/7eG0RWUROHeq9FfiTkl/1EveR7mUmQzbXXHhPSaC
saj5HmW9h2BW6y6RWpPN6SyD5KhbEqfYI/ZYYT1yHpNGrwcSqribwG1vViT/aJtD
QWe2RJ3yVaEquMN5SYc8eNGEq6whqkFl4oKmE3hnlyfIo24dVNAfKz1cnIe79ccZ
iO47WeMJWPBm0GEUCRkZtyl72KIWt3gairDr+w/9bf+laVmsz8AClyLlf2jkJSGY
tnwD177LnyZyKQZLAgMBAAGjggIsMIICKDAOBgNVHQ8BAf8EBAMCBaAwHQYDVR0l
BBYwFAYIKwYBBQUHAwEGCCsGAQUFBwMCMAwGA1UdEwEB/wQCMAAwHQYDVR0OBBYE
FEEdBTkaZpOwlzuzjxwe9Yx2cLLmMB8GA1UdIwQYMBaAFLu8w0el5LypxsOkcgwQ
jaI14cjoMFcGCCsGAQUFBwEBBEswSTAiBggrBgEFBQcwAYYWaHR0cDovL3IxMC5v
LmxlbmNyLm9yZzAjBggrBgEFBQcwAoYXaHR0cDovL3IxMC5pLmxlbmNyLm9yZy8w
MwYDVR0RBCwwKoILKi5waWNnby5uZXSCCCoueHp0Lm1lgglwaWNnby5uZXSCBnh6
dC5tZTATBgNVHSAEDDAKMAgGBmeBDAECATCCAQQGCisGAQQB1nkCBAIEgfUEgfIA
8AB2AKLjCuRF772tm3447Udnd1PXgluElNcrXhssxLlQpEfnAAABkwa221wAAAQD
AEcwRQIgMXaXU+bHONOk9xA45VYb/wQrfazmftkwBPf/QpWgMOsCIQCbbnErkvcj
vpkzicYqdHRQBMopbFoUmKasWapcXiKQOQB2AObSMWNAd4zBEEEG13G5zsHSQPaW
hIb7uocyHf0eN45QAAABkwa24zEAAAQDAEcwRQIgcFuSE/cDSfVcUVcquoHEBdz0
4iCoZNxZxnPQsQlwaRMCIQDfm1mFzrxp9To2m15PlTn6eooZQNFcHSprSC7EErnQ
vzANBgkqhkiG9w0BAQsFAAOCAQEAzJd4bJzojWgLxjb4HVryfDMBESkJPYZEmLvk
V0AwkSXMR5XeLj4Hb/+2LZFAW2LHRRpR+YnjZtrvM84GQF08adcJa1T5g3a2sYD/
bm3XZGOtWmGABqqOG6+mKtk4t7b+xLZkda8LDeDdiVWDR5+i5xHKim0ADikGgHu6
6FaY93YVdjcbgCZiGtjgzaj1ECvXdRHpCLDnP6vtVu30bH8C/OFxUM7Fc7K/NniL
oOGxgFsQNwP1Ok4W8Zn81yKbN5J6EV/EFzWlD8FCr/aeXQG3/CkWZ04NcRdtjtUg
cS82CfdGsRbvq83sTqNR7H3tKUqXK/D8r3ixF5Wmpu6tgATkig==
-----END CERTIFICATE-----
subject=CN = picgo.net
issuer=C = US, O = Let's Encrypt, CN = R10
---
No client certificate CA names sent
Peer signing digest: SHA256
Peer signature type: RSA-PSS
Server Temp Key: X25519, 253 bits
---
SSL handshake has read 3139 bytes and written 386 bytes
Verification: OK
---
New, TLSv1.3, Cipher is TLS_AES_256_GCM_SHA384
Server public key is 2048 bit
Secure Renegotiation IS NOT supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
Early data was not sent
Verify return code: 0 (ok)
---
---
Post-Handshake New Session Ticket arrived:
SSL-Session:
Protocol : TLSv1.3
Cipher : TLS_AES_256_GCM_SHA384
Session-ID: F6CD8EC55A283B8F078DF73F8961F0360D952D57C9D59EA938EFA04386E70533
Session-ID-ctx:
Resumption PSK: F0C35F7EC2BCA8D6E428B8BDE66143553F6743E9C4C2C245C680D9BCEB178DC91165A0455A456CEDA57BB9A1407FC1FD
PSK identity: None
PSK identity hint: None
SRP username: None
TLS session ticket lifetime hint: 7200 (seconds)
TLS session ticket:
0000 - c2 47 17 7a da ac 54 1d-71 12 97 ee 7d a5 cb 7a .G.z..T.q...}..z
0010 - 76 f8 b1 d4 f6 40 51 9e-b6 e0 14 38 09 fa 09 d0 v....@Q....8....
0020 - f1 81 d1 5b 5c bd a4 b0-34 34 33 30 56 69 70 15 ...[\...4430Vip.
0030 - 06 13 2b 37 1b a1 0a 9a-5f 25 98 7f c1 84 09 7c ..+7...._%.....|
0040 - b9 5b 9c 0c 33 d0 b8 79-74 1e d1 67 63 0c 02 e8 .[..3..yt..gc...
0050 - 9c a2 0d 74 b4 23 4d e0-7c 48 ea 91 7c 11 33 8f ...t.#M.|H..|.3.
0060 - 62 41 47 98 e1 98 d9 b5-5b 41 f0 14 3e 71 2e 84 bAG.....[A..>q..
0070 - 0b f1 f5 5b e1 a4 a4 73-26 81 8f 11 90 ef fd 32 ...[...s&......2
0080 - 57 94 f4 5c 82 c9 22 54-c4 98 ce 9c 39 10 75 5e W..\.."T....9.u^
0090 - da cc 49 78 9c e2 08 58-5d 4e 84 f4 97 52 74 29 ..Ix...X]N...Rt)
00a0 - 97 aa c0 25 93 db 79 b1-fa 90 3f 61 7e ce 72 b1 ...%..y...?a~.r.
00b0 - 5d 59 61 2b 5e db 41 ae-ba 35 eb 34 8e ca 53 be ]Ya+^.A..5.4..S.
00c0 - ba d4 6c 16 92 8d f1 89-52 d5 30 80 a5 5a 38 f5 ..l.....R.0..Z8.
00d0 - 84 2b d3 5a 5c 49 e6 bb-e2 7c 4a c9 80 70 d8 3a .+.Z\I...|J..p.:
Start Time: 1731679393
Timeout : 7200 (sec)
Verify return code: 0 (ok)
Extended master secret: no
Max Early Data: 0
---
read R BLOCK
220 mail.xzt.me ESMTP (Super Email)
421 4.4.2 mail.xzt.me Error: timeout exceeded