- Edited
Fail2ban manager: ban hosts that cause multiple authentication errors
GitHub
Use case:
Simply add an sshd service to prevent blasting
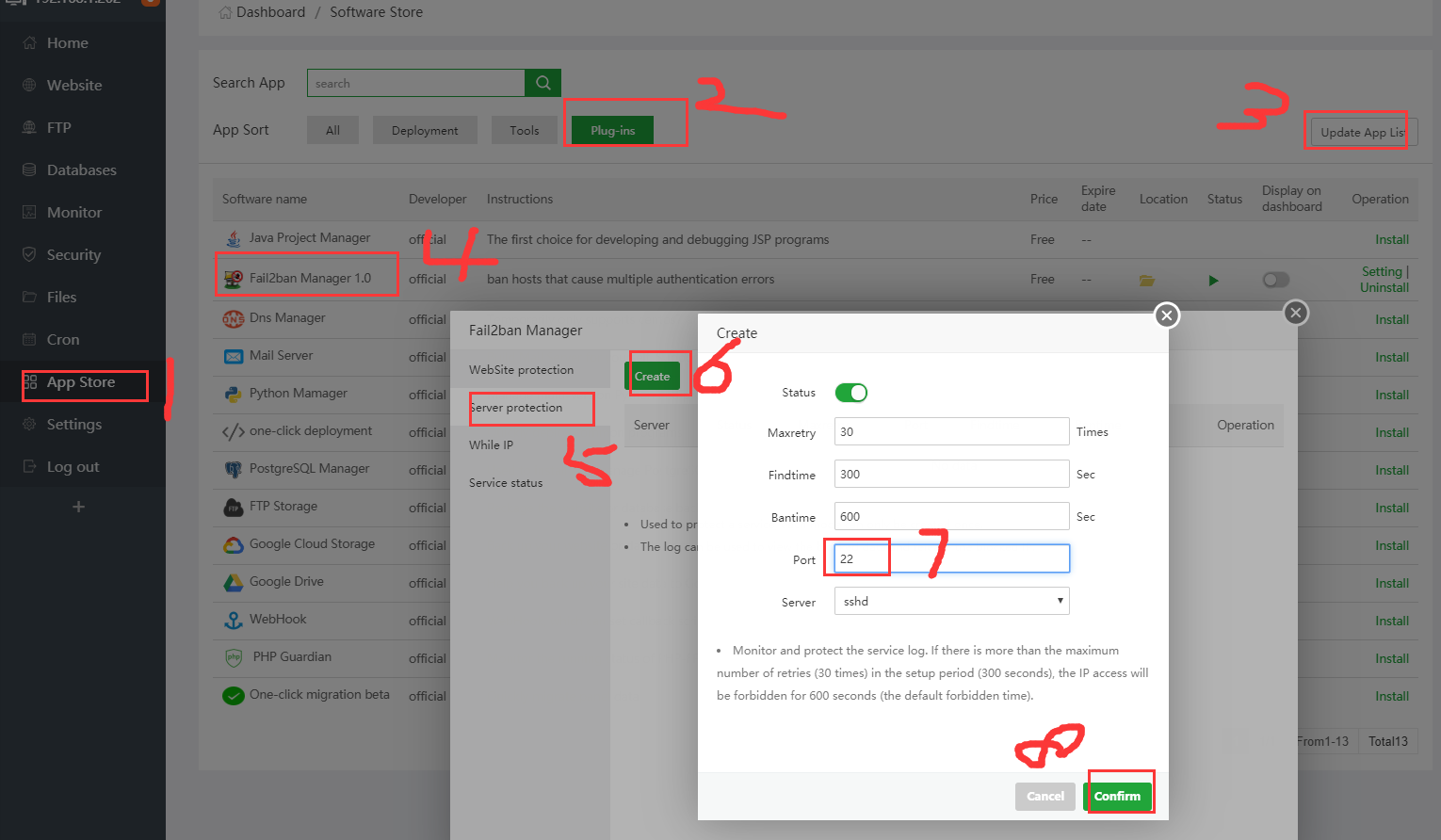
View the current rule's work
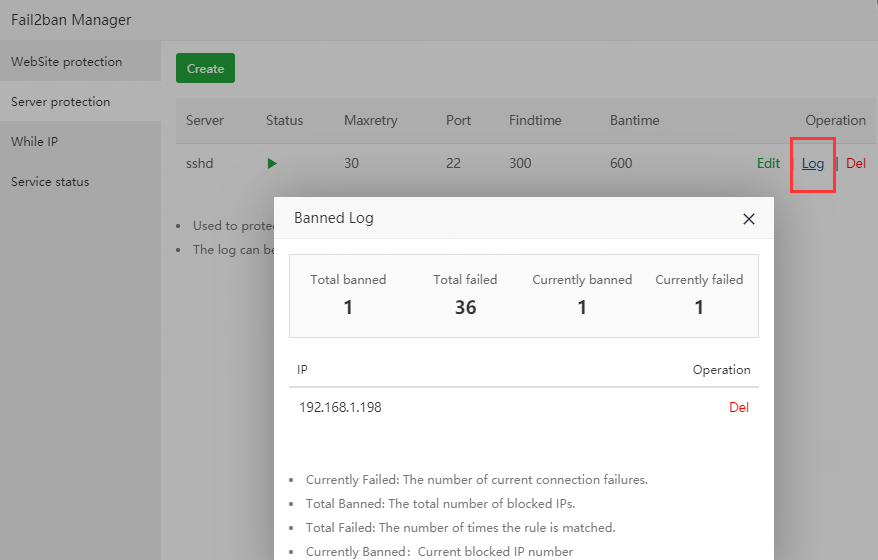
Fail2ban manager: ban hosts that cause multiple authentication errors
GitHub
Use case:
Simply add an sshd service to prevent blasting

View the current rule's work

#SOLVED
##I need to restart the fail2ban-client then the new rules takes effect!
Hi, thanks for this cool feature.
I tried to create a sshd rule (maxretry = 5, findtime= 300, bantime= 60000) on my server, then use another server to access the SSH with incorrect password for more than 10 times. But seems like nothing happen, no IP was ban.
I click on the Log of the rule but just showing Acquisition Failed.
Additionally, when i add whitelist IP, in a new line in Whitelist IP tab, it keeps showing IP format is incorrect.
nephilax
What Linux distribution are you using?
can you run this command and show me the the result?
cat /etc/fail2ban/jail.local
aaPanel_Jose
Hi, i am using CentOS Linux release 7.6.1810 (Core)
#DEFAULT-START
[DEFAULT]
ignoreip = 127.0.0.1/8
bantime = 600
findtime = 300
maxretry = 5
banaction = firewallcmd-ipset
action = %(action_mwl)s
#DEFAULT-END
#jasticker.com-cc-START
[jasticker.com-cc]
enabled = true
filter = aaP_jasticker.com_cc
port = 80,443
maxretry = 10
findtime = 300
bantime = 600
action = %(action_mwl)s
logpath = /www/wwwlogs/jasticker.com.log
#jasticker.com-cc-END
#sshd-START
[sshd]
enabled = true
filter = sshd
port = 8288
maxretry = 5
findtime = 300
bantime = 6000
action = %(action_mwl)s
logpath = /var/log/secure
#sshd-END
#nginx-404-start
[nginx-404]
enabled = true
port = http,https
action = %(action_mwl)s
filter = nginx-404
logpath = /www/wwwlogs/jasticker.com.log
maxretry = 7
findtime = 300
bantime = 14400
#nginx-404-end
nginx-404-error i manually added in after all working well.
As per my edit in the original post, it's working well after i restarted the fail2ban-client. Before that, when i run fail2ban-client status, i am not able to see the sshd and cc rules.
nephilax
It seems that your allocation is not a problem. Do you have any errors in the command line execution
fail2ban-client reload ?
aaPanel_Jose
Nope, reload showing ok. Maybe just my server got problem. Let's see any other user facing same issue. At least now mine is working fine now after restarted fail2ban-client.
Hi aaPanel_Jose
However, the whitelist IP seems unable to add through the white list tab. I am not just add my own server public IP manually into jail.local
nephilax
Please update to 1.1 to fix this issue
I add a rule to one for one of my websites.
then I wanted to change it, but I receive a log error.
I deleted the rule and when I try to create a new rule for the same domain, I`m getting an error
*The log file does not exist and cannot be created*
Any idea how to solve it?
aaP_esales2000
Add postfix directly to the Server protection of fail2ban
aaPanel_Kern
I added the postfix rule successfully.
But, I want to add a rule for the web server as well.
The first time, it gives to add successfully a rule,
But, I`m getting a log creation error on two conditions:
aaP_esales2000
WebSite protection Add related sites
Rule file: /etc/fail2ban/jail.local
Please do not change it at will, the panel may not be recognized after the change
aaPanel_Kern
I notice that if i restart the Apache, i`m getting an error:
Apache rule configuration error:
AH00526: Syntax error on line 8 of /www/server/panel/vhost/apache/mydomain.conf:
CustomLog takes two or three arguments, a file name, a custom log format string or format name, and an optional "env=" or "expr=" clause (see docs)
aaP_esales2000
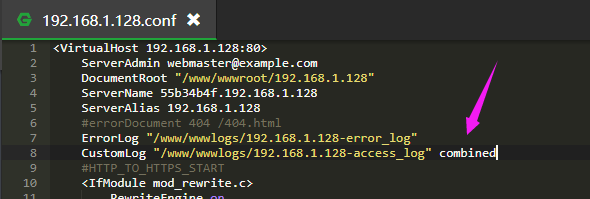
default configuration
combined
aaPanel_Kern
Working great.
By adding "combined" it solved all issues.
Thank you and have a great weekend
some hacker is sending emails from root@mydomain and root@locahost
May 5 15:46:28 vmi613070 postfix/qmgr[18763]: 4E8C6160062A: removed
May 5 15:46:28 vmi613070 postfix/local[18768]: C56E71601880: to=<root@localhost>, relay=local, delay=16772, delays=16772/0.52/0/0, dsn=2.0.0, status=sent (delivered to mailbox)
May 5 15:46:28 vmi613070 postfix/qmgr[18763]: C56E71601880: removed
May 5 15:46:28 vmi613070 postfix/local[18765]: 0CBA3160072E: to=<root@localhost>, relay=local, delay=26749, delays=26748/0.52/0/0, dsn=2.0.0, status=sent (delivered to mailbox)
May 5 15:46:28 vmi613070 postfix/qmgr[18763]: 0CBA3160072E: removed
May 5 15:46:28 vmi613070 postfix/local[18768]: 9DB4D160059E: to=<root@localhost>, relay=local, delay=9583, delays=9583/0.53/0/0, dsn=2.0.0, status=sent (delivered to mailbox)
May 5 15:46:28 vmi613070 postfix/qmgr[18763]: 9DB4D160059E: removed
May 5 15:46:28 vmi613070 postfix/local[18767]: 3FCC816007A7: to=<root@localhost>, relay=local, delay=23291, delays=23290/0.53/0/0, dsn=2.0.0, status=sent (delivered to mailbox)
May 5 15:46:28 vmi613070 postfix/qmgr[18763]: 3FCC816007A7: removed
May 5 15:46:28 vmi613070 postfix/local[18765]: C346B1600552: to=<root@localhost>, relay=local, delay=34139, delays=34139/0.54/0/0, dsn=2.0.0, status=sent (delivered to mailbox)
May 5 15:46:28 vmi613070 postfix/qmgr[18763]: C346B1600552: removed
May 5 15:46:28 vmi613070 postfix/local[18768]: B9B1D16000EB: to=<root@localhost>, relay=local, delay=34140, delays=34139/0.54/0/0.01, dsn=2.0.0, status=sent (delivered to mailbox)
May 5 15:46:28 vmi613070 postfix/qmgr[18763]: B9B1D16000EB: removed
May 5 15:46:28 vmi613070 postfix/local[18765]: 95BCF160149C: to=<root@localhost>, relay=local, delay=4029, delays=4029/0.55/0/0, dsn=2.0.0, status=sent (delivered to mailbox)
May 5 15:46:28 vmi613070 postfix/qmgr[18763]: 95BCF160149C: removed
May 5 15:46:28 vmi613070 postfix/local[18767]: AFAAE1600113: to=<root@localhost>, relay=local, delay=28708, delays=28708/0.55/0/0.01, dsn=2.0.0, status=sent (delivered to mailbox)
May 5 15:46:28 vmi613070 postfix/qmgr[18763]: AFAAE1600113: removed
May 5 15:46:29 vmi613070 postfix/local[18766]: B222B1601485: to=<root@localhost>, relay=local, delay=21982, delays=21981/0.03/0/0.91, dsn=2.0.0, status=sent (delivered to mailbox)
.....
May 5 15:46:28 vmi613070 postfix/master[18761]: daemon started -- version 3.4.7, configuration /etc/postfix
May 5 15:46:28 vmi613070 postfix/qmgr[18763]: warning: /etc/postfix/main.cf, line 707: overriding earlier entry: myhostname=mail.mydomain.com
May 5 15:46:28 vmi613070 postfix/pickup[18762]: warning: /etc/postfix/main.cf, line 707: overriding earlier entry: myhostname=mail.mydomain.com
May 5 15:46:28 vmi613070 postfix/qmgr[18763]: 8361616007ED: from=root@vmi613070.hostingdomain.com, size=493, nrcpt=1 (queue active)
May 5 15:46:28 vmi613070 postfix/trivial-rewrite[18764]: warning: /etc/postfix/main.cf, line 707: overriding earlier entry: myhostname=mail.mydomain.com
What is the best way to block it?
aaP_esales2000
In the Linux system, the root user can send emails by default. However, in order to enhance system security, you can restrict the root user from sending mail by configuring the mail server or changing the settings of the mail client.
Here are some ways you can restrict the root user from sending mail:
Configure mail server: You can configure mail server to prevent root user from sending mail. Specifically, you can create a mail filtering rule on the mail server to prevent the root user from sending mail. For example, in a Postfix mail server, you would add the following to the /etc/postfix/main.cf file:
smtpd_sender_restrictions = check_sender_access hash:/etc/postfix/sender_access
Then, add the following to the /etc/postfix/sender_access file:
root REJECT
This will change mailx's default sender address, preventing root from sending mail.
Change the email address of the root user: You can change the email address of the root user to prevent the root user from sending emails. For example, on an Ubuntu system, you can edit the /etc/aliases file and change root's email address to a non-real email address:
root: /dev/null
This will prevent the root user from sending mail.
Note that changing the configuration of the root user may affect the normal operation of the system. Therefore, make sure you know what you are doing and back up important data before changing your system configuration.