CQT You can't run a regex to get only the ip's so i lost 10 seconds to do that for you.
106.13.82.54
114.67.113.78
49.235.141.203
203.195.235.135
107.170.104.125
1.204.116.48
159.65.158.30
218.94.156.130
205.185.123.139
121.204.185.106
37.49.224.65
207.244.247.251
51.75.171.171
180.250.248.169
205.185.115.40
154.204.27.249
84.124.204.154
106.124.135.232
49.234.122.94
144.172.73.40
222.186.15.158
128.199.100.254
207.244.247.192
122.51.66.219
114.67.102.106
49.234.83.240
223.167.13.128
119.45.114.87
120.201.125.204
150.129.67.50
144.172.79.8
45.162.216.10
106.75.13.192
222.186.30.218
222.186.52.39
219.250.188.165
168.197.31.14
144.172.73.41
118.89.69.159
82.118.236.186
112.35.57.139
50.70.229.239
85.209.0.103
37.49.224.39
218.92.0.216
58.246.94.230
144.172.79.7
220.78.28.68
124.30.44.214
51.178.55.92
222.186.30.167
186.147.129.110
117.50.8.61
181.30.99.114
222.186.31.166
115.78.4.219
218.255.86.106
222.186.15.115
222.186.42.137
218.92.0.223
216.83.45.162
218.92.0.221
111.229.176.206
222.186.30.76
218.92.0.219
222.186.42.155
222.186.30.112
94.172.225.26
218.92.0.215
93.146.233.226
193.70.12.219
112.17.184.171
222.186.31.83
222.186.42.136
218.92.0.220
36.111.171.108
119.18.194.168
222.186.190.14
222.186.42.7
222.186.180.142
109.115.187.31
222.186.30.57
106.124.141.108
139.215.217.181
61.177.172.102
109.244.101.169
182.252.133.70
222.186.15.62
144.172.79.5
222.186.30.35
222.186.31.127
222.186.180.130
186.215.235.9
152.136.141.254
14.142.143.138
112.35.62.225
111.229.78.120
106.12.215.244
23.129.64.0
89.248.168.0
89.248.168.255
212.70.149.0
212.70.149.255
212.70.149.0
212.70.149.255
And i make enough time to upload a list with the ip's tested.
https://we.tl/t-iTQ8A105T8
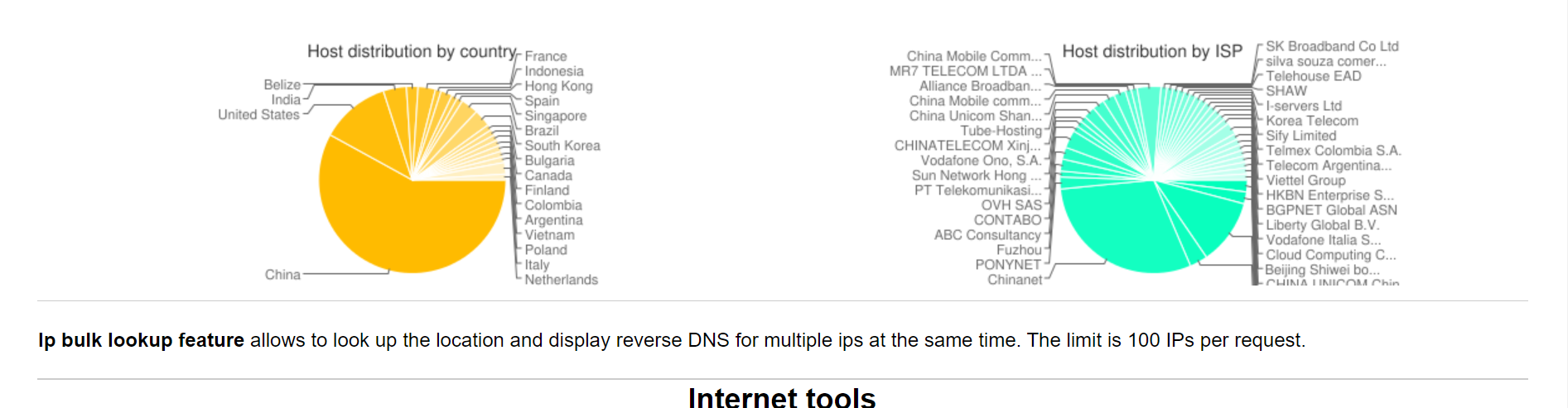
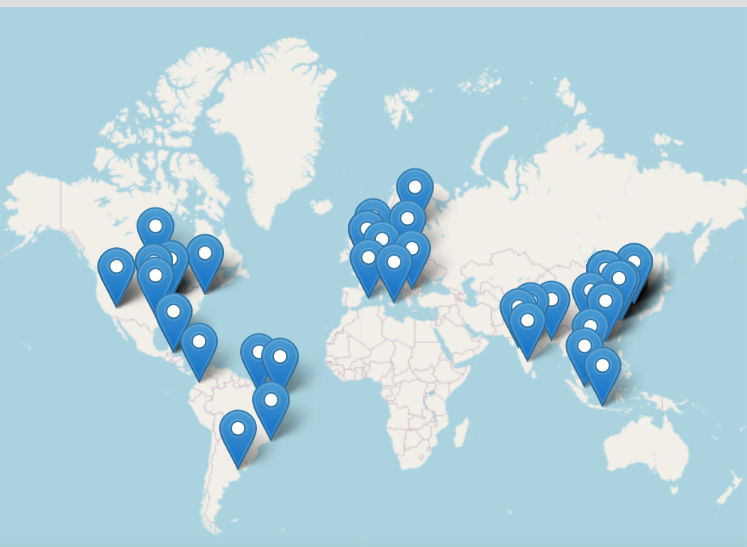
How are this ip's from BT panel when are random countries? And mostly are clean ip's not even fucking VPN's.
If someone would want to steal data will do it on long run and over vpn's you know is smarter that way.