We use various tools and we have a firewall from its log, we can see where the attacks come from, plus some other network monitoring tools and you can use this to determine where and from which network the IPs come.
https://www.ultratools.com/tools/ipWhoisLookup but we still have many far-reaching options that I do not want to explain further here (company secrets).
Source: whois.apnic.netIP Address: 106.12.215.244
% [whois.apnic.net]
% Whois data copyright terms http://www.apnic.net/db/dbcopyright.html
% Information related to '106.12.0.0 - 106.13.255.255'
% Abuse contact for '106.12.0.0 - 106.13.255.255' is 'ipas@cnnic.cn'
inetnum: 106.12.0.0 - 106.13.255.255
netname: Baidu
descr: Beijing Baidu Netcom Science and Technology Co., Ltd.
descr: Baidu Plaza, No.10, Shangdi 10th street,
descr: Haidian District Beijing, 100080
admin-c: SD753-AP
tech-c: SD753-AP
country: CN
mnt-by: MAINT-CNNIC-AP
mnt-lower: MAINT-CNNIC-AP
mnt-irt: IRT-CNNIC-CN
mnt-routes: MAINT-CNNIC-AP
status: ALLOCATED PORTABLE
last-modified: 2015-01-28T09: 58: 01Z
source: APNIC
irt: IRT-CNNIC-CN
address: Beijing, China
e-mail: ipas@cnnic.cn
abuse-mailbox: ipas@cnnic.cn
admin-c: IP50-AP
tech-c: IP50-AP
auth: # Filtered
remarks: Please note that CNNIC is not an ISP and is not
remarks: empowered to investigate complaints of network abuse.
remarks: Please contact the tech-c or admin-c of the network.
mnt-by: MAINT-CNNIC-AP
last-modified: 2017-11-01T08: 57: 39Z
source: APNIC
person: Supeng Deng
nic-hdl: SD753-AP
address: No.6 2nd North Street Haidian District Beijing
country: CN
phone: + 86-10-58003402
fax-no: + 86-10-58003402
e-mail: zhangyukun@baidu.com
mnt-by: MAINT-CNNIC-AP
last-modified: 2016-11-01T08: 04: 01Z
source: APNIC
% Information related to '106.12.192.0/18AS38365'
route: 106.12.192.0/18
descr: Baidu
country: CN
origin: AS38365
notify: zhangyukun@baidu.com
mnt-by: MAINT-CNNIC-AP
last-modified: 2017-12-21T08: 06: 02Z
source: APNIC
% Information related to '106.12.192.0/18AS55967'
route: 106.12.192.0/18
descr: Baidu
country: CN
origin: AS55967
notify: zhangyukun@baidu.com
mnt-by: MAINT-CNNIC-AP
last-modified: 2017-12-21T08: 06: 02Z
source: APNIC
% This query was served by the APNIC Whois Service version 1.88.15-SNAPSHOT (WHOIS-US4)
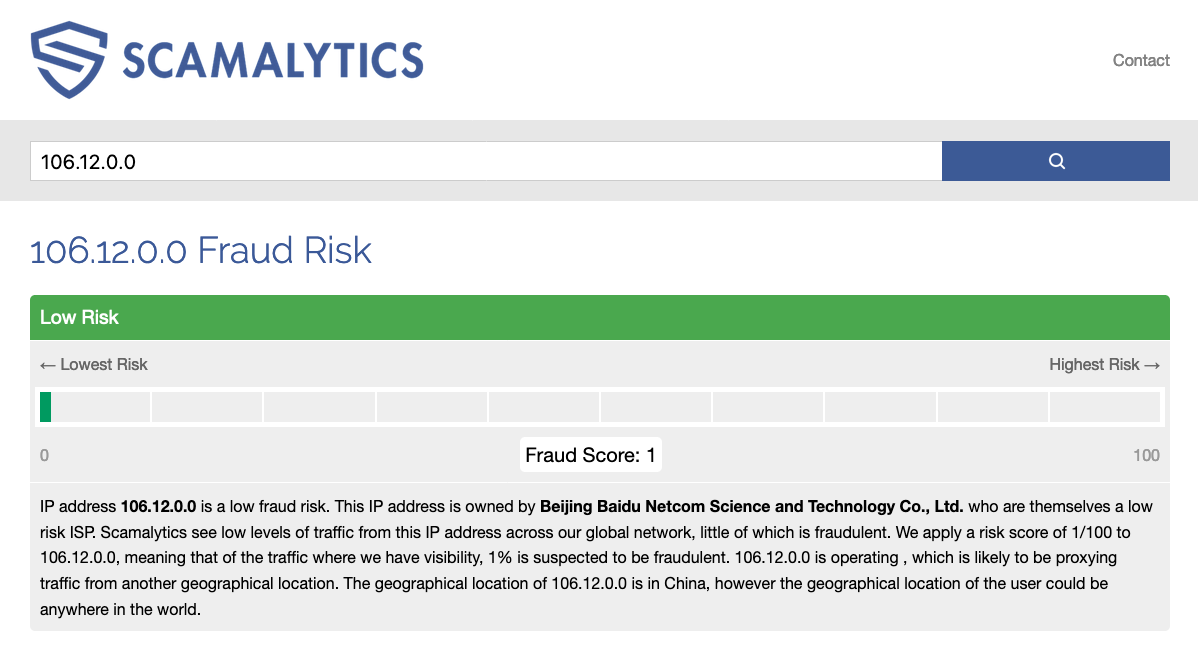
almost all attacks come from the network from 106.12.0.0 - 106.13.255.255
and a few more of which we trace up to
netname: Baidu
descr: Beijing Baidu Netcom Science and Technology Co., Ltd.
descr: Baidu Plaza, No.10, Shangdi 10th street,
descr: Haidian District Beijing, 100080
could trace back, using vpn / proxyserver.