You are right, it is a big problem. I watch logs in CloudFlare and I see unwanted and unexpected traffic from bots mainly from China, Singapore, Russia and other countries searching for phpmyadmin url, for searching files, etc. With some rules I try to avoid them (to reduce) but of course spam not stopping here because spam is going also direct to IP (unbound domainds, etc, I have set a default site setted and I see all traffic and IPs...). Fail2Ban is fully of IPs and I have all ports disabled (and enabled to my proxy IP for restricted-safe access) except 443.
Hacking attacks with and through aaPanel
- Edited
Maybe we should find an alternative panel for better security or wait a big update...
Oh yes. I finally found one! I also use FastPanel, I agree that is a perfect alternanative with quick ticket support and more stability. Some specs lacks but is very good on speed, uses different accounts for sites, very low use of memory and mainly Apache + Nginx is perfect (backend go very fast). General FastPanel has logic but needs a better deploy, some parts are a litle mysterious.
I AGREE 100%  !!!
!!!
heh FastPanel didn't know that one, going to test it!
CQT Suggestion! Connect the sys firewall and geoip under one tab. Write Config in such a way that both get the DB from one source (folder) and can access it at the same time. Furthermore, the IP and the entire IP range are queried, which can then be blocked using a button, but which the user can decide for himself whether only the individual IP (Geoip is blocked or the entire network of the IP operator). Then integrate the NGINX firewall into the whole. Because on the one hand it is very confusing, and I also think that everything does not work together so harmoniously.
Which is the full procedure to integrate them all?
Thank you very much
Make a unified response, our panel is open source, github address: https://github.com/aaPanel/BaoTa
In addition I read most of the responses, is some targeted scanning, such as phpmyadmin use of port 888, redis use of port 6379, if you do not use phpmyadmin or redis, you can remove these ports in the panel security, if you use phpmyadmin, redis, I also do not recommend that you use the default If you use phpmyadmin and redis, I don't recommend you to use the default ports, you can modify them to other ports that are not used by other services. In addition, the service permissions on the panel are accessed by localhost|127.0.0.1 by default, except for the ports that are needed on the panel such as 8888 80 443.
We attach great importance to user feedback on security-related issues, because we ourselves are a company that does security operations and maintenance, and if our products are questioned, all our employees will feel bad about it!
Also if you encounter security related information during use, you can email our team directly to anyone! My email address is: power@aapanel.com
- Edited
Jimmy Maybe we should find an alternative panel for better security or wait a big update...
Cyberpanel is much better. They hired Rack911 to help tighten the security. Keep in mind, they were not badly off in terms of security. https://rack911labs.ca/research/security-analysis-of-alternative-control-panels/
aaPanel should follow suit.
aapanel_power We attach great importance to user feedback on security-related issues, because we ourselves are a company that does security operations and maintenance, and if our products are questioned, all our employees will feel bad about it!
You need an independent third-party company to conduct a security audit of aaPanel. There will always be smart asses out there and that's why an independent audit is important.
- Edited
I personally am sorry for speaking harshly, but I do that (I mean to say sorry) because I am human and also a developer and I know how hard it is to maintain something, especially opensource, but I am a perfectionist, and you should do to, because your software is serving a big share of people. Also, you have to understand that your words should follow your actions if you want them to have actual meaning. After a year of comments in this thread I did not see any actions in terms of this matter. There is a vulnerability here. Once your users install the panel using the bt.cn node, instantly their cover is blown and they are suddenly exposed to the world and easy exploitable with automated payloads, this is serious stuff. Thank you!
aaP-aris Once your users install the panel using the bt.cn node, instantly their cover is blown and they are suddenly exposed to the world and easy exploitable with automated payloads, this is serious stuff. Thank you!
Unfortunately, aaPanel is rebrand of BT Panel and I think aaPanel developers have to wait for BT Panel developers to do stuff. So in this case, they have to request BT Panel developers to work on it.
- Edited
Nope. You are 100% wrong here (my opinion). I don't agree with you for 2 reasons. First reason: it's open source, so they can do whatever they want and second reason: all they had to do is change the installation script and remove bt.cn nodes. The installation script is not even a part of the main repository, it's a separate file downloaded from their official rebranded website, not the bt.cn version!
@aaP-aris and @Jimmy guys thanks a mil for the fastpanel hint. Haven't had much time to try it, but so far what I have tested I am really enjoying it!
Pros:
- Super fast performance;
- Uses the systems packages instead of cumbersome install scripts that break everything;
- Well achieved user interface, haven't found any bugs;
Cons:
- No chance of changing the default user or create a new "super user" and remove the current;
- No ability to choose what software to install in the beginning;
However, I have used dnf to remove ... exim, dovecot and a couple of other services it installs by default, it removes the services and appears to be working perfectly.
Again, the performance of the panel itself is brilliant, I'm very much enjoying it. Cheers
Also they have good support. It's free and they respond quickly. I've tried it!
Another good alternative if you deploy websites via Vultr is Plesk (Web Admin SE). It's FREE for 3 domains and it has all the features of the paid version!
CQT You can't run a regex to get only the ip's so i lost 10 seconds to do that for you.
106.13.82.54
114.67.113.78
49.235.141.203
203.195.235.135
107.170.104.125
1.204.116.48
159.65.158.30
218.94.156.130
205.185.123.139
121.204.185.106
37.49.224.65
207.244.247.251
51.75.171.171
180.250.248.169
205.185.115.40
154.204.27.249
84.124.204.154
106.124.135.232
49.234.122.94
144.172.73.40
222.186.15.158
128.199.100.254
207.244.247.192
122.51.66.219
114.67.102.106
49.234.83.240
223.167.13.128
119.45.114.87
120.201.125.204
150.129.67.50
144.172.79.8
45.162.216.10
106.75.13.192
222.186.30.218
222.186.52.39
219.250.188.165
168.197.31.14
144.172.73.41
118.89.69.159
82.118.236.186
112.35.57.139
50.70.229.239
85.209.0.103
37.49.224.39
218.92.0.216
58.246.94.230
144.172.79.7
220.78.28.68
124.30.44.214
51.178.55.92
222.186.30.167
186.147.129.110
117.50.8.61
181.30.99.114
222.186.31.166
115.78.4.219
218.255.86.106
222.186.15.115
222.186.42.137
218.92.0.223
216.83.45.162
218.92.0.221
111.229.176.206
222.186.30.76
218.92.0.219
222.186.42.155
222.186.30.112
94.172.225.26
218.92.0.215
93.146.233.226
193.70.12.219
112.17.184.171
222.186.31.83
222.186.42.136
218.92.0.220
36.111.171.108
119.18.194.168
222.186.190.14
222.186.42.7
222.186.180.142
109.115.187.31
222.186.30.57
106.124.141.108
139.215.217.181
61.177.172.102
109.244.101.169
182.252.133.70
222.186.15.62
144.172.79.5
222.186.30.35
222.186.31.127
222.186.180.130
186.215.235.9
152.136.141.254
14.142.143.138
112.35.62.225
111.229.78.120
106.12.215.244
23.129.64.0
89.248.168.0
89.248.168.255
212.70.149.0
212.70.149.255
212.70.149.0
212.70.149.255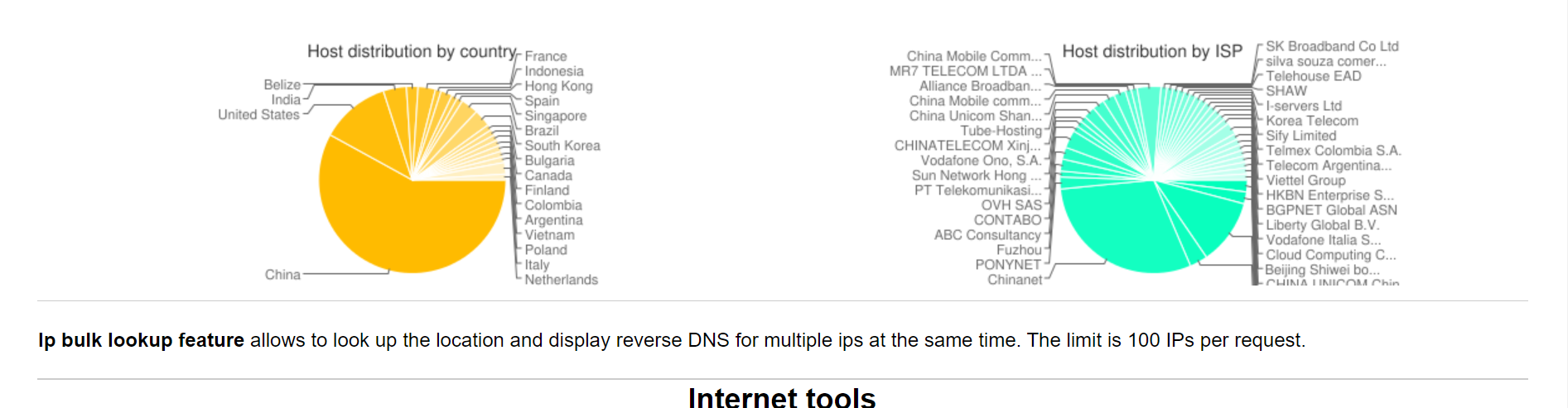
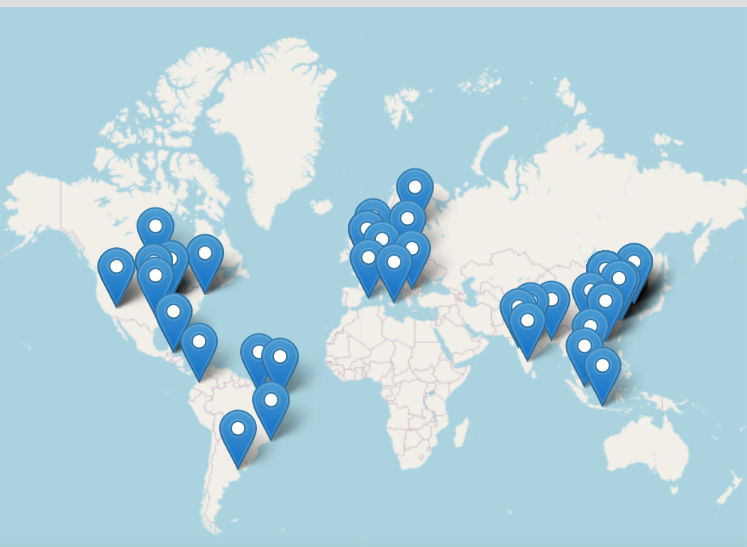
And i make enough time to upload a list with the ip's tested.
How are this ip's from BT panel when are random countries? And mostly are clean ip's not even fucking VPN's.
If someone would want to steal data will do it on long run and over vpn's you know is smarter that way.
Jimmy That is mostly because IPv4 is reused big times, on OVH i had 600 ssh requests because the ip was reused so don't blame the tool, i'm not sure if this panel is safe but for sure on a production server i won't use any panel not even the paid one's, this one is good for fast dev deployment so is a usefull tool. Who use a panel for production and talk about security and employers that do that and that and they can't make a proper log common sense lol. Look at GoDaddy's cPanel hacking to understand how secure it was.
With this one you have the source code atleast but i still not recommend to use any panel in a production server.
- Edited
Port scanning and brute force is also common, This is nothing related to panel. As this panel is having more than a million installation, definitely it will be a target for bad boys.
Some prevention for production servers
- Go with SSH login and disable root once everything is done.
- Secure shared memory by adding tmpfs /run/shm tmpfs defaults,noexec,nosuid 0 0 in /etc/fstab
- Install fail2ban and activate server protection for sshd, ftp, mysql etc
- NGINX WAF for website.
- Add cloudflare if possible and block ip having threatscore above 14.
- Add captcha challenge for countries like china, and other if needed.
- Change ssh port to anything between 100 and 1024.
- Make Sure No Non-Root Accounts Have UID Set To 0
- Enable SSH Login for Specific Users Onl
Anyone can add points to this as its good for everyone.
